Before going into the different types of cyber-attack that we should be aware of in 2023, first of all, I want to explain what a cyber-attack is to anyone who might not really understand this term but is currently reading this article. So what exactly is a cyber-attack? A cyber-attack is any attempt to obtain unauthorized access to a computer, computing system, or computer network with the intention of causing harm. Cyber-attacks try to modify, block, delete, alter, or steal the data stored in computer systems to disable, disrupt, destroy, or control them. The persons behind any cyber-attacks are known as cybercriminals, threat actors, or hackers.
Now that we clearly understand what a cyber-attack is, let us go into the types of cyber-attacks that we should be aware of in 2023.
TYPES OF CYBER ATTACKS
Phishing Attack
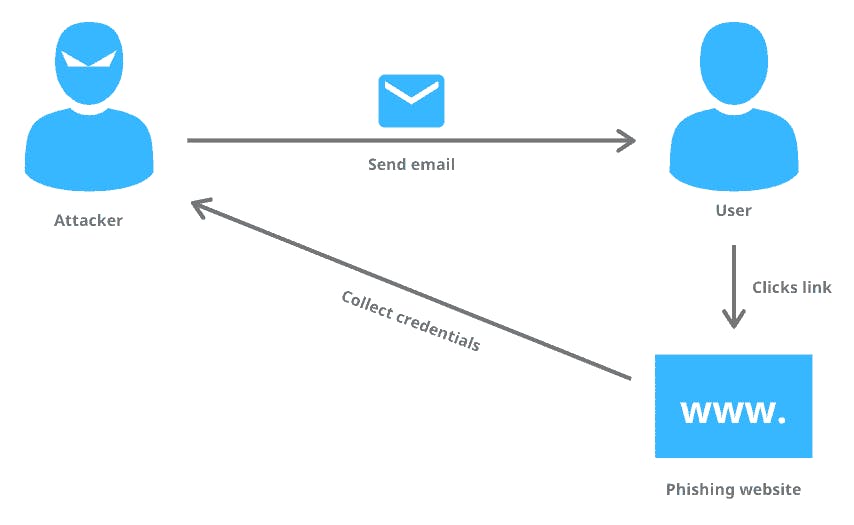
This is one of the most common types of attack in our world today. In a phishing attack, personal information is the typical objective of this kind of attack, which typically involves emails. It entails sending emails that upon close examination appear to be from a trustworthy source but are not. Other types of phishing include links or attachments that, when clicked, drive you to websites where they fool you into disclosing personal information or downloading malware onto your machine. By doing so, attackers gain access to confidential information and account credentials.
An example of a phishing attack is spear phishing. In spear phishing, attackers put effort into learning about their targets to generate messages that are both individualized and useful. This makes spear phishing incredibly difficult to detect and even more difficult to defend against. The goal of phishing is to get sensitive and personal information.
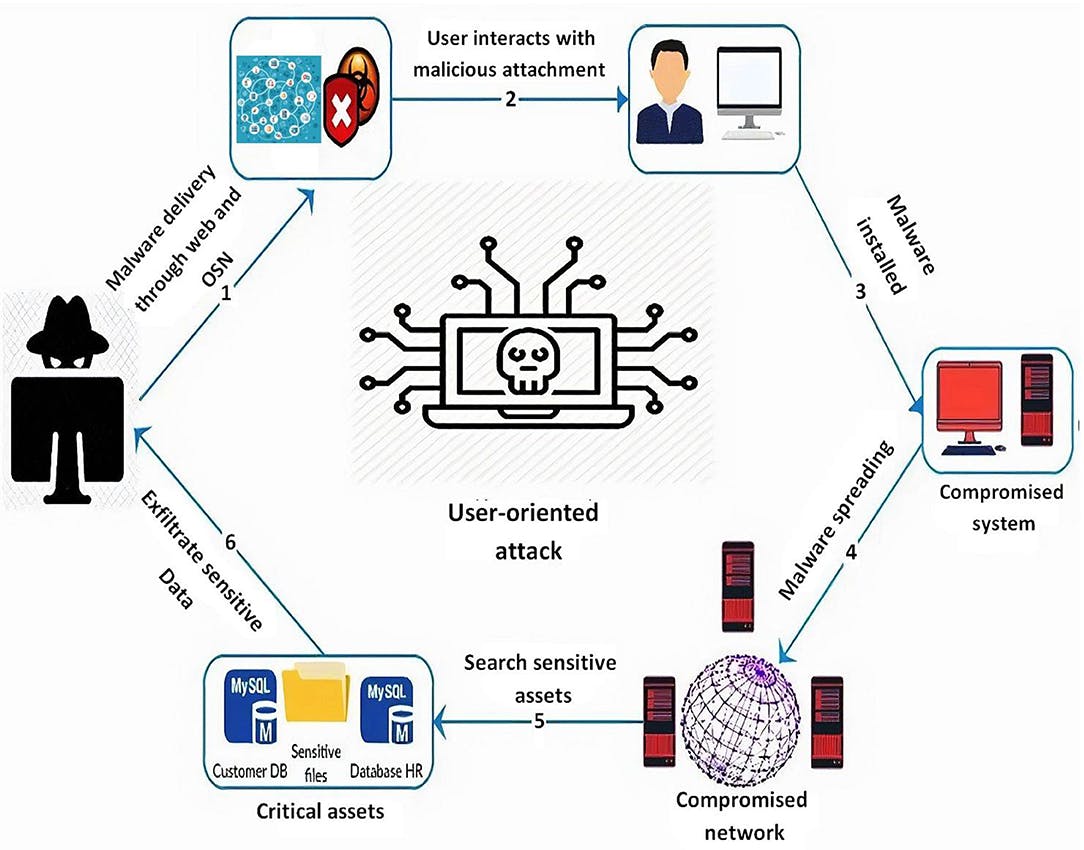
Malware Attack
Malware refers to malicious software that is created with the intent to harm a computer, network, or server such as spyware, ransomware, viruses, and worms. Malware is initiated when a user clicks on a malicious link or attachment, which results in the installation of hazardous software. A malware attack can result in the restriction of Access to critical network components through ransomware, personal information being stolen by sending data from the hard drive through spyware, Disruption of individual components, and rendering the system unusable.
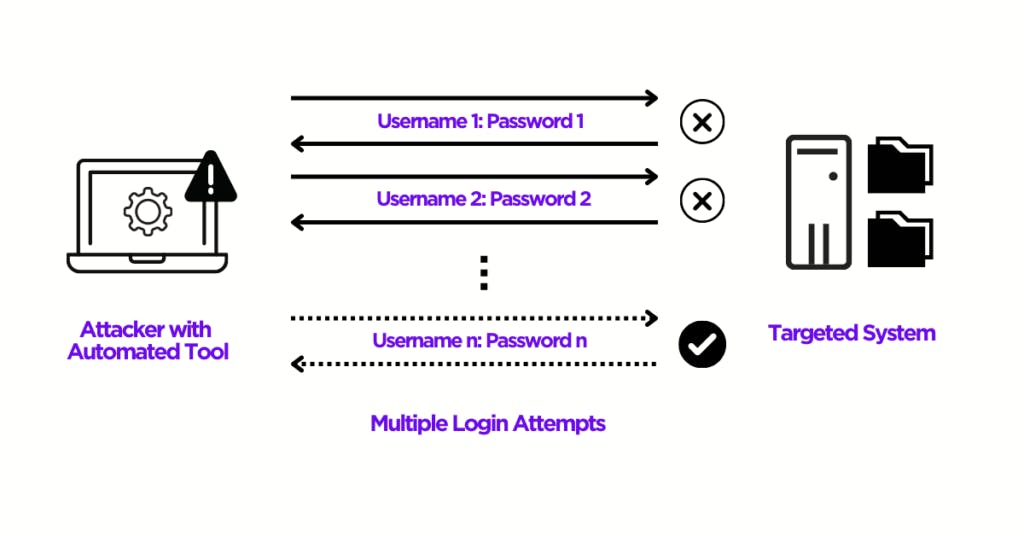
Password Attack
This type of cyberattack is responsible for a lot of data breaches in the world in which hackers try to compromise user account authentication by getting access to a password-protected computer, account, or file. They utilize automated password attack software to speed up password cracking and guessing. The most common methods are brute forcing, password spraying, and dictionary attack.
Distributed Denial of Service (DDoS) Attack
In this type of attack, threat actors restrict users from accessing associated websites, network resources and online services. A DDoS attack overwhelms the targeted organization's resources with HTTP requests and traffic, preventing legitimate users from accessing one or more of its services, and resulting in severe interruption.
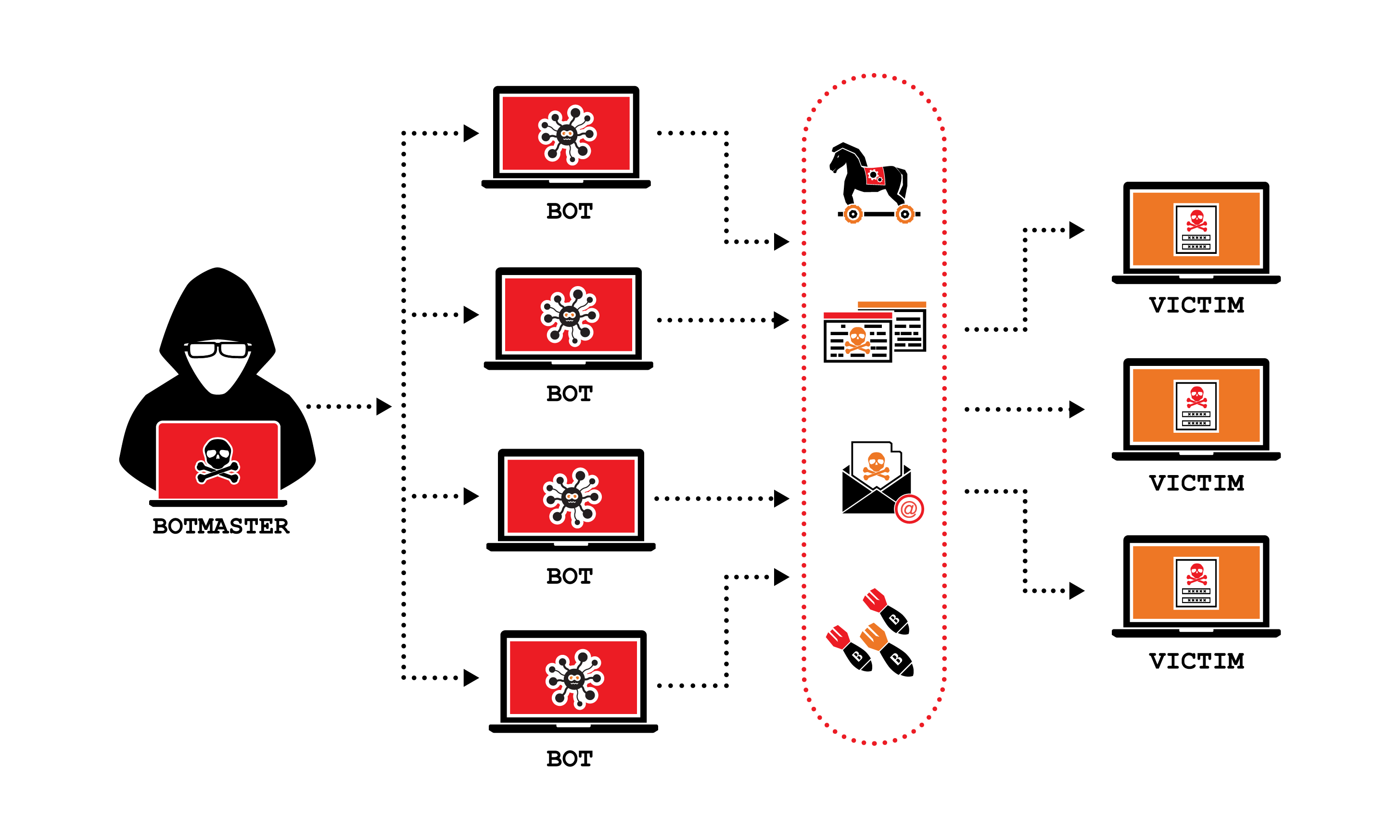
Internal threat
Internal actors, such as current or former employees, contractors, vendors, or partners, who pose a threat to a company because they have direct access to the network, sensitive information, and intellectual property (IP), as well as knowledge of business procedures, company policies, or other information that could help carry out such an attack, are known as insider threats. Insider threats might be carried out deliberately or accidentally. Whatever the motivation, compromised enterprise systems and data integrity, confidentiality, and/or availability are the ultimate results.