Social engineering is one of the most popular means by which threat actors use to exploit individuals and organizations. Although people are becoming more aware of social engineering attacks yet more and more people still fall victim to these threat actors.
Social engineering is a term that refers to the ability of something or someone to influence the behavior of a person or group of people. In cybersecurity, it refers to a collection of techniques used to deceive internal users into performing specific actions or revealing confidential information. Social engineering scams are designed to exploit how people think and act. As a result, social engineering attacks are particularly effective at manipulating a user's behavior. Once an attacker understands what motivates a user's actions, they can effectively deceive and manipulate the user.
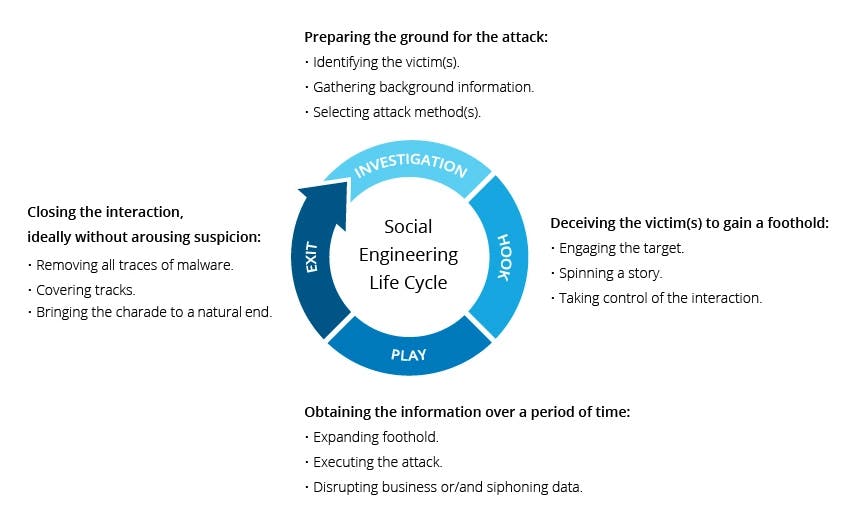
Attacks using social engineering take place in one or more steps. A perpetrator first looks into the target to gather background information, such as possible points of entry and inadequate security measures, needed to carry out the attack. The attacker then makes an effort to win the victim's trust to motivate later actions that violate security protocols, like disclosing private information or granting access to vital resources. The fact that social engineering relies on human error rather than flaws in software and operating systems makes it particularly dangerous. Legitimate user errors are much less likely to be predicted, making them more difficult to spot and stop than a malware-based intrusion. Social engineers want victims to feel a certain way. They want to create a sense of Trust, Urgency, Kinship, Authority, Disdain, Power, Stress, and Pity.
The most popular techniques used in social engineering are phishing, pretexting, baiting, quid pro quo, and tailgating.
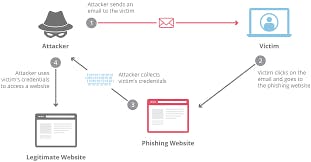
- Phishing: phishing is the most popular form of social engineering where attackers deceive people into revealing sensitive information or installing malware such as ransomware. This is usually done via emails that contains links to malicious sites or malicious attachment.
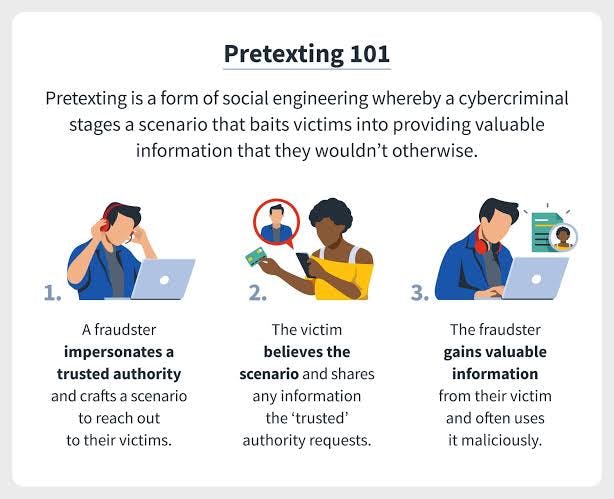
- Pre-texting: Pretexting is a type of social engineering where an attacker tries to persuade a victim to divulge crucial data or grant access to a service or system. This type of attack is distinctive in that the con artists create a story or pretext in order to deceive the victim.
- Baiting: This is a form of social engineering attack where an impostor uses a deceptive promise to entice a victim into a trap where they risk having their financial and personal information stolen or having malware installed on their system. A malicious attachment with an intriguing name could be the trap.

- Quid pro quo: The Latin phrase "quid pro quo" means "something for something." In other words, a QUID PRO QUO attack in the context of social engineering is when a social engineer offers a service, usually "tech support" in exchange for access to secure information. A good example would be if an attacker called your phone pretending to be a technical support agent from one of your service providers. He or she will offer you assistance, but it will only be useful if you are having a problem.

- Tailgating: Tailgating is a type of social engineering attack in which an unauthorized person physically gains access to a restricted area, possibly one that is password-protected, where they may steal confidential data, cause property damage, compromise user credentials, or even infect computers with malware. For example A person who claims they’ve lost their work ID or forgotten it at home, so that you grant them admittance. This is usually done in large organization where many of the staffs barely know each other.

Best practices to prevent social engineering attack
Don't open emails from suspicious sources
Use two-factor or multi-factor authentication
Be wary of tempting offers for example messages that say you have won something you didn't apply for and you need to click on a link to accept it.
Using Antivirus/ Anti Malware on your devices
Cybersecurity education / training
Never use the same password for different accounts
Define Roles and Verify Identities
Updating your softwares and operating systems when needed
